Given the number of industries impacted by cybercrime, and the ongoing evolution of cyberattacks, one might expect cyber security to be a top concern for most organizations. However, would it surprise you to know that only 50 percent of businesses actually have a cyber security plan in place?
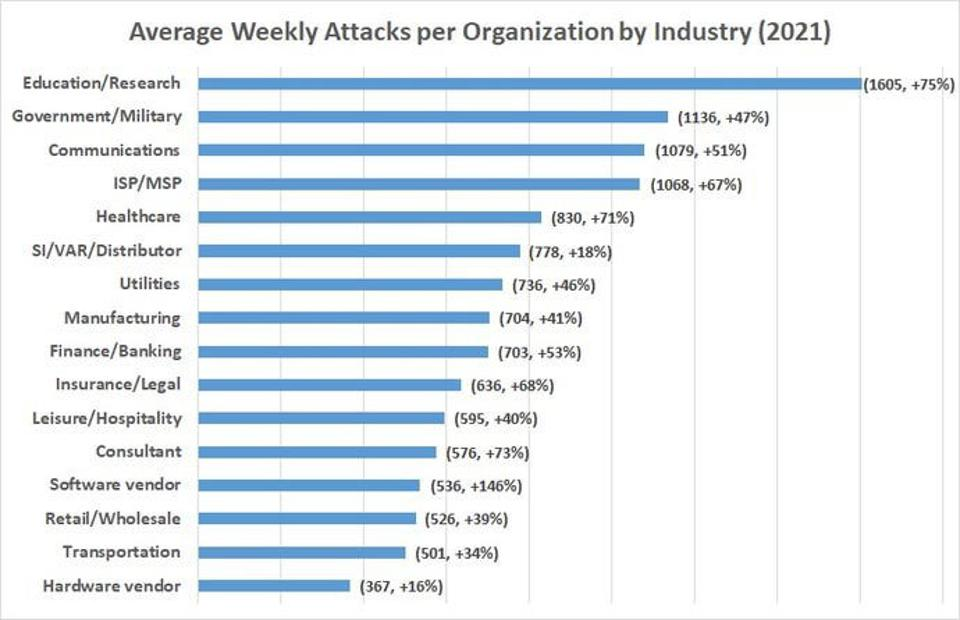
Source: Check Point Software Technologies, Blog: Cyberattacks, 2021.
According to a recent Forbes article, not only are many organizations woefully under-equipped to deal with a cyber security threat, half of them don’t even have a functional cyber security plan. This statistic is alarming when you consider that cybercriminals attempting to breach an organization’s network via external attack are successful 93 percent of the time — usually in as little as two days.
Even more concerning is the fact that the most significant cyber security impacts result from the inadvertent actions of employees. Specifically, according to the FBI’s Internet Crime Complaint Center (IC3), over $43 billion has been lost through Business Email Compromise (BEC) attacks since 2016, where cybercriminals gain access to secure networks through phishing and social engineering.
So, while many agree that cybercrime is a threat and organizations need to protect themselves, it appears that there is significant opportunity for improvement — and opportunity for those interested in cyber security careers.

 Live Chat
Live Chat